
Unlock GPU Power: The NoPorts Solution for AI Arbitrage
Download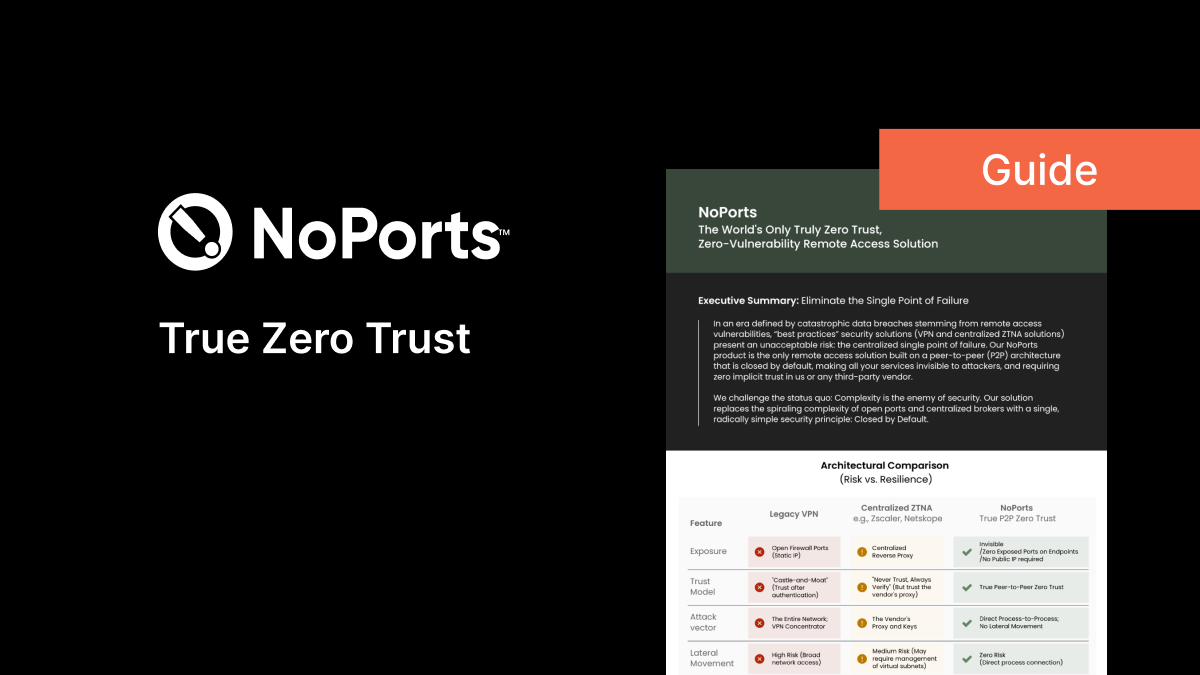
NoPorts - The Only Zero Trust Solution
Download
Guide: Preemptive Security for Banking
Download
Guide: Disrupting the Kill Chain - A Preemptive Defense Mapped to the MITRE ATT&CK Framework
Download
Case Study: Streamlining Precision Agriculture IoT with NoPorts
Download
Guide: How Are You Securing Your AI?
Download
Guide: Be Digitally Invisible with NoPorts from Atsign
Download
Overview: Using Zero Trust Sockets to Simplify Network Security
Download
Overview: Mitigating MiTM Risks & Ensuring Data Integrity with NoPorts
Download
Use Case: Digi IX40 & NoPorts for Secure Remote Access
Download
Overview: How to Make Your Cloud Invisible with NoPorts
Download
Overview: Simplify IoT and OT Security with NoPorts
Download
Use Case: A More Secure MQTT with NoPorts
Download
Overview: Simplify Your Networks with Policy Management with NoPorts
Download
Overview: How to Fortify Your DMZ Right Now with NoPorts
Download
Guide: An Analysis of Bastion Cloud Access Security Options
Download
Revolutionizing Network Security with Atsign's Zero Trust Approach
Download

