For decades, the VPN (Virtual Private Network) has been the go-to method for secure remote access, extending network perimeters and protecting data in transit. And when you’re connecting to a single network, VPNs still have their place.
But today’s environments are different. It’s rare that an organization’s infrastructure is contained within a single network. They are generally segmented by design for security, compliance, and operational independence. Development teams need access to isolated test environments, while simultaneously pushing code to a secure staging system and pulling metrics from an analytics database in yet another zone. Now add in vendors, managed AI services, and non-human agents (like inference nodes or CI/CD systems). Each needs tightly scoped access—often across organizational or even geopolitical boundaries—without violating isolation.
This is where the traditional VPN model and mesh-based overlay networks start to unravel, introducing complexity, security gaps, and logistical nightmares. For a development team trying to pull data from a secure, air-gapped system while simultaneously pushing updates to a staging environment, this becomes a frustrating dance of disconnecting and reconnecting, managing multiple credentials, or worse—creating dangerous bridges between networks that compromise their intended isolation.
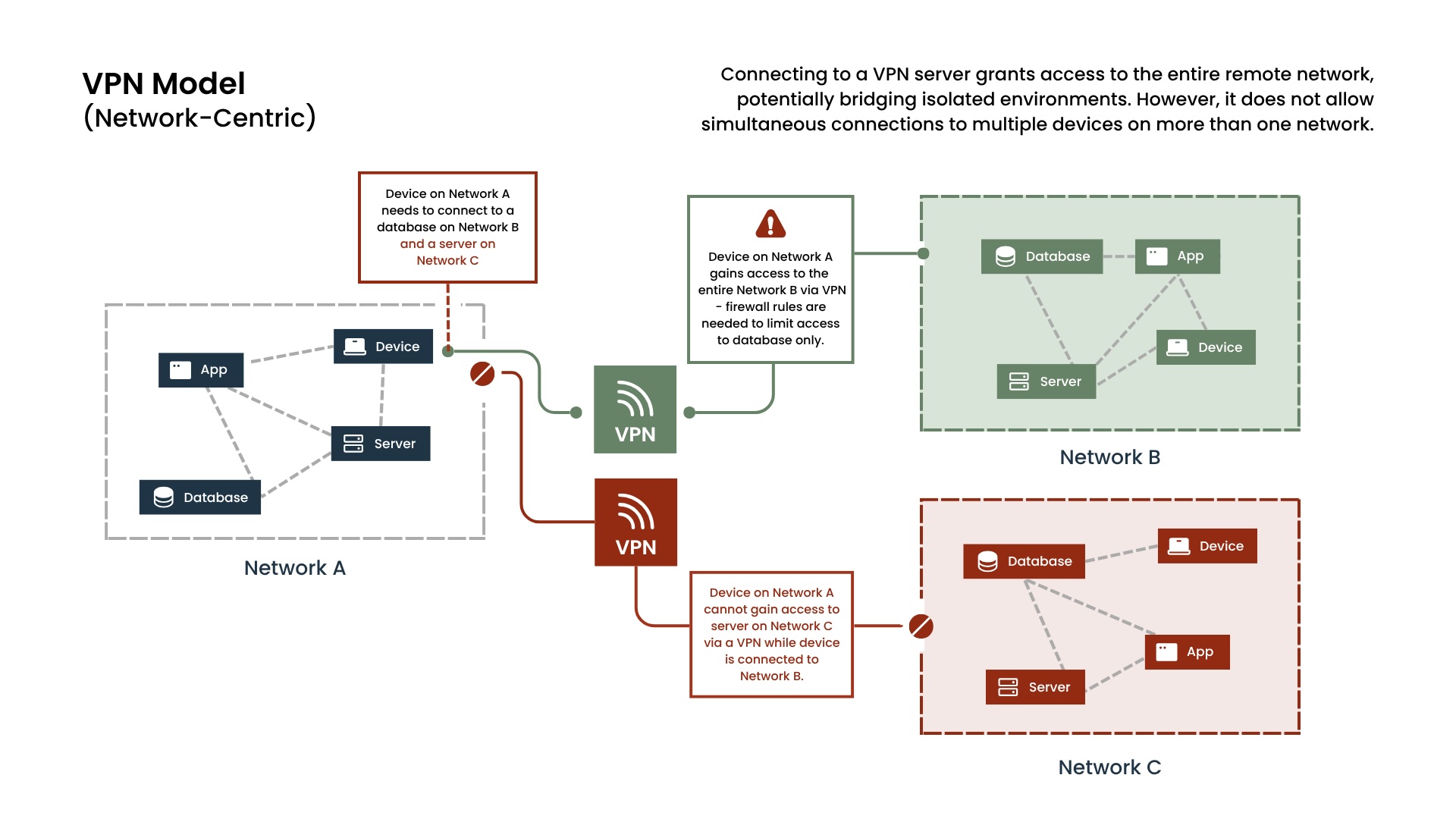
The Network-Centric Trap
The core challenge lies in the network-centric nature of VPNs and mesh overlay network solutions. They're designed to connect you to a network. If you need to be "on" several different, intentionally segregated networks at the same time, you're forced into an unsustainable model. Attempting to run multiple VPNs concurrently on a single device is often impossible and turns your device into a risky conduit, effectively joining these separate networks and opening up massive security vulnerabilities.
This isn't just a theoretical issue; it's a reality for enterprises. Organizations are increasingly segmenting their infrastructure for security, compliance, and operational efficiency. Test environments are air-gapped from production. For example, operational technology (OT) networks are often isolated from IT networks by design. Partner ecosystems demand secure, yet separate, access. The more isolated your critical assets become, the more apparent the limitations of network-centric connectivity.
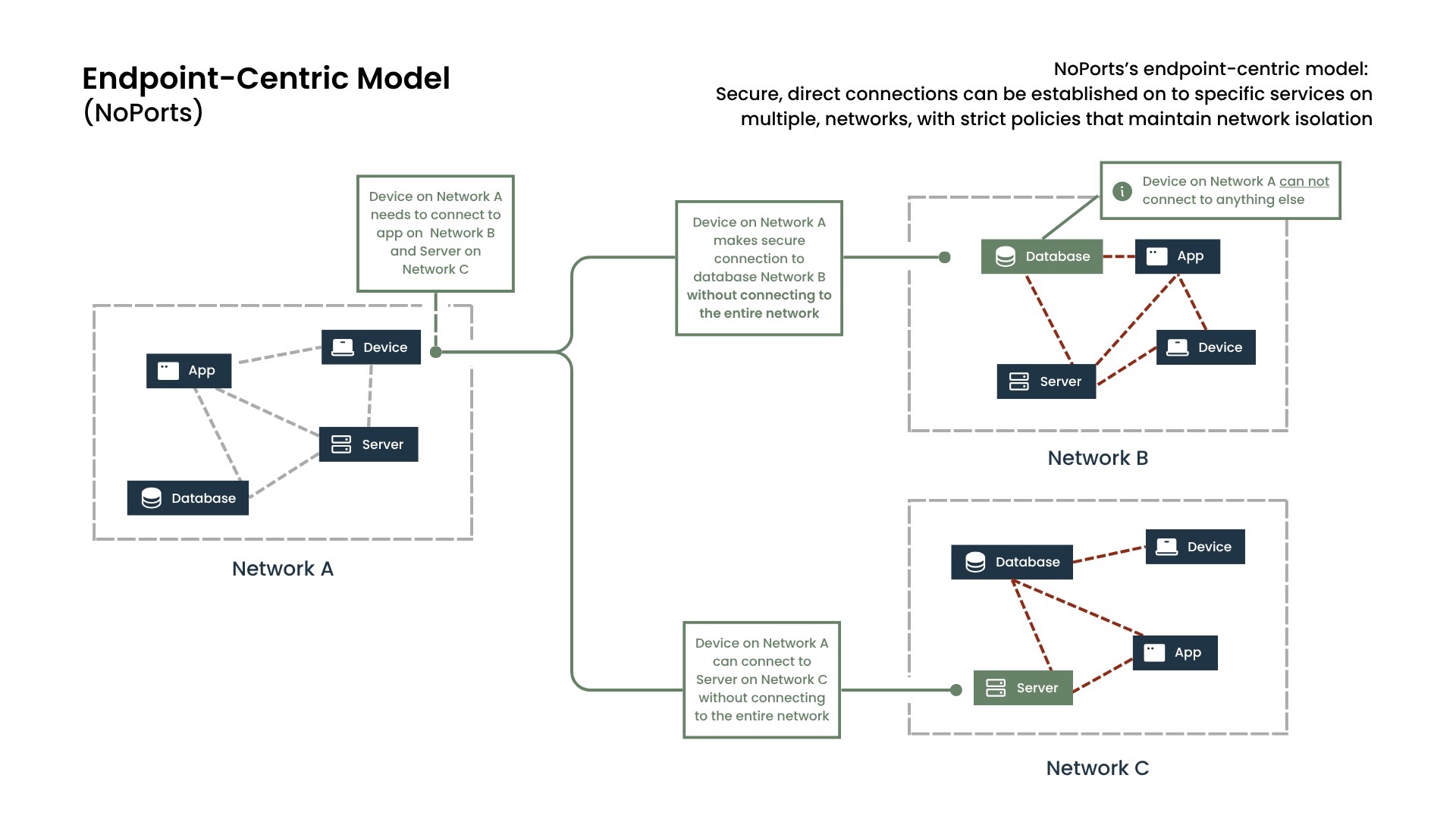
Introducing a Smarter Way: Endpoint-Centric Connectivity with NoPorts
This is where a new paradigm emerges: endpoint-centric connectivity. Instead of joining entire networks, this approach focuses on establishing secure, direct connections between the specific applications or services that need to communicate, regardless of which network they reside on. Think of it as opening a highly secure, point-to-point conversation between two specific applications, without either of the underlying networks being aware of each other. This is exactly what we’ve built with NoPorts.
This model provides granular control through a simple, yet powerful, security framework. Connections are based on a digital identity, ensuring that only authenticated applications and systems can communicate. A policy then governs what each identity can access, similar to a VIP guest list for your network. While you can have broad rules such as, "Let all of the engineers on the crm app's dev team connect to all of the crm test system's APIs," you can also have very precise rules such as, "Let our accounting app talk only to the server's database on port 5432, and absolutely nothing else."With NoPorts, a single device or application can seamlessly:
- Access multiple isolated systems simultaneously, speeding up development and testing cycles without compromising security.
- Interact with various external partners securely, each on their own distinct network, eliminating credential sprawl and connection conflicts.
- Bridge OT and IT environments without creating a wide-open network pathway.
This approach maintains the inherent isolation of your networks, drastically reducing the attack surface. There are no broad network bridges to exploit, just tightly controlled, direct connections created by NoPorts.
Take the next step
Secure and efficient connectivity across isolated networks is a strategic imperative. Ready to move beyond the limitations of traditional VPNs?
Ready to move beyond the limitations of traditional VPNs?
- Start your free trial of NoPorts today and experience endpoint-centric access that's secure by default, invisible by design.
- Contact us for a personalized demo to discuss your specific use cases and learn how NoPorts solves complex connectivity challenges.






